Password Search FAQ
Password search
Strong cryptographic algorithms and methods (e.g. AES, SHA, PBKDF2) are in use by modern software for password verification and data encryption. Hashing algorithms are commonly applied multiple times making known vulnerabilities inapplicable even for outdated algorithms. Passwords are usually salted in order to block any pre-image attacks or generation of rainbow tables.
That is why exhaustive password search is the only real password recovery option for such cases.
Search basics
Password search is a kind of a guessing game. Password candidates are generated based on a search range (attack) selected and verified one by one till the right password is found. Search range configuration / setup is very important. Password can be as simple as "1234" for example, but letters-only search is not going to be successful in any timeframe in contrast to digits-based search, obviously.
Search time
There is no way to predict overall search time required as several attacks might need to be used till result is achieved. Search time for an attack is equal to a number of passwords to check divided by a search speed. Search speed is hardware limited and there is no way to increase it by much. Thus the only way to shorten search time is to narrow the search range using additional details.
Mixed attacks »
Mixed attacks are a key feature of our tools that offers unique search range setup precision and flexibility. They can be used to narrow search range using known parts, patterns, etc. Passwords like "P4ssword" can be discovered very slow with 8 chars brute-force search. Mixed attack: 1 char 'A..Z' + 1 char '0..9' + 6 chars 'a..z' is more than 2500 times faster! And mixed attack based on a dictionary and char replacement 'A to 4' is an even smaller option in this case. Another mixed attack example shows how to combine word list with numbers and special chars to search for a seemingly simple password pattern that is otherwise hard to find using commonly available methods.
Default attacks:
Our tools were preset with a dozen of default attacks. These attacks are based on common password generation techniques and intended to be basic examples of brute-force, dictionary and mixed type of attacks. You can try all or some of them, but it is the best to setup your attacks (or at least try to modify existing ones) for the task in hand as password patterns are very personal. Many search options and modifications existing today were proposed by our customers over the years, thus feel free to request additional options / mods to extend the flexibility of our search setup.
Search complexity:
Password candidates are generated as a composition of parts (chars, words) and it is required to process all possible combinations. The number of combinations equals to the multiplication of the number of items in each part. Four-digit pin complexity is equal to 10*10*10*10=10000=10^4 (10 to the power of 4) variants from 0000 to 9999. Five-digit pin is 10 times more complex and requires 10 times longer search time. There are 26*26 combinations of a two lowercase Latin alphabet letters, but 52*52 (4 times) lower/upper case variants. Attack complexity limit is 2^128 = 340,282,366,920,938,463,463,374,607,431,768,211,456 passwords to examine and it is more than a lifetime with any hardware. With a charset of digits only it is around 38 digits brute-force attack or 18-19 with all printable characters.
Best way to start:
We believe that a test case (e.g. test file) with known password is the best way to start. In just few minutes you can check format compatibility, see full cycle from attack setup to "recovered password" dialog. It is also much easier to setup initial attacks / search settings with a known target in mind.
Number of attacks to dispatch:
Common practice is to process password search attacks sequentially. Parallel dispatching of attacks is a unique feature available in our tools. Small blocks of password candidates are generated based on selected number of attacks and send to be processed. Search speed (passwords per second) remains the same as it is hardware limited, but a more diversified approach might yield results faster.
Output attacks to a file:
This option allows you to save list of password candidates to a file (UTF8 encoded plain text file) without any password verification calculations. This can be used as a simplest method to verify attacks settings or to generate a new wordlist based on one or several attacks. Wordlist generator is quite fast, thus big enough sample for settings verification will be ready in just a few seconds and you can stop the process to avoid extra disk load. If your goal is wordlist generation, please note that some attacks (brute-force for example) can generate multi-GB or multi-TB files.
Password search progress:
Password search progress is saved as position within current attack for current task every 5-10 minutes. This allows you to switch from file to file and from attack to attack with just several last minutes of search discarded. Note: password recovery progress is not used in trial version.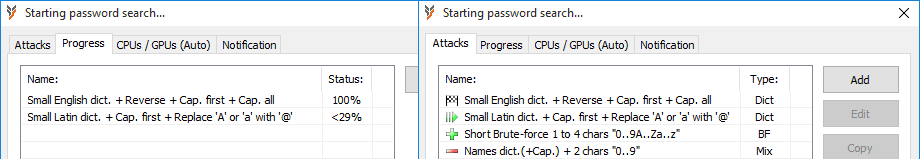
Recovered password:
As soon as correct password is found program stops, displays it using special dialog and saves current search position. There is no way for a search engine to pass the password. Recovered password is not saved for security reasons, but it can be recovered again rapidly by restarting from saved position if program / computer was forced to shutdown for any reason (system update, power failure, etc.). You can also setup post-search notification.
Multi-PC processing:
Mixed attacks are also designed to allow multi-PC processing without network setup and maintenance headaches. Any search range can be easily split into several blocks to be processed in parallel. A simple PIN search 0000..9999 can be split into 0000..4999 + 5000..9999 with two mixed attacks: 1 char "0..4" + 3 char "0..9" on PC1 and 1 char "5..9" + 3 char "0..9" on PC2. In additional to multi-computer processing this technique is also useful for out of order processing (if some blocks are more likely to contain the right password), etc.
It is worth noting that a single license key cannot be used on more than one PC.
GPU Utilization:
Our tools use standard OpenCL API to interact with GPU cards. Free tools like "GPU Caps Viewer" can be used to verify all OpenCL platforms / devices available on your system. "clinfo" command line tool is also pre-installed with all modern GPUs, thus you can export current OpenCL parameters into a file with a single command: "clinfo > clexport.txt". OpenCL API is part of all GPU drivers for many years, but some special drivers (mining, AI, etc.) might not support OpenCL API by design. Clear (re)installation of the latest "standard" drivers is the first step to fix any GPU issues.
Processing in blocks:
Password candidates are processed in blocks. CPU blocks are equal in size and selected to be processed within 1-2 seconds. GPU blocks are variable in size and can take up to 5 minutes to complete . Search status dialog shows sample passwords and search speed based on current blocks sent to CPU and GPU, thus sample passwords can be out of sequence and it can take up to 5-10 minutes for all results to be summed into full search speed.
Error in OCL / OCL Build
Please check the latest program version and / or download and install the latest drivers for your Graphics Processing Unit (GPU). AMD and Nvidia drivers are usually up to date, but it is not uncommon to have 5-6 years old Intel HD GPU drivers installed. "AMD Clean Uninstall Utility" can be used to reinstall drivers and fix settings errors. We suggest to uninstall unused GPU drivers as well if AMD card was replaced with NVIDIA card or vice versa.
Error in GPU thread / nvopencl.dll...
Errors in nvopencl.dll or GPU driver failures are usually due to a power shortage, overheating or overclocking. Cooling issues are easy to test with vendor tools or a number of free tools like "GPU-Z". NVIDIA and AMD cards default shut-off temperature is ~80-90C. Power shortage can be a factor as well. Please check your card recommended minimum. Password recovery is the hardest task for GPU, thus extra 100-200W are more appropriate. CPU/GPU page can also be used to set CPU threads count manually to lower CPU power consumption and heat output.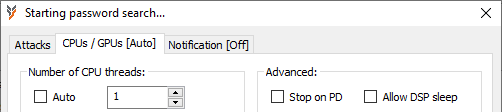
Many GPUs are factory overclocked and some are just not designed to work under constant heavy load, thus it might be necessary to downclock (10-20% can make a big difference) such devices for a stable issue-free performance. Tools like "MSI Afterburner" are available to control GPU core speed as well as other settings like fan speed, power consumption, etc.
Another option is to use CPU/GPU page to set GPU rest (cool off) time (in percent of block processing time).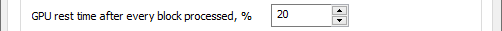
All trademarks are the property of their respective holders.
