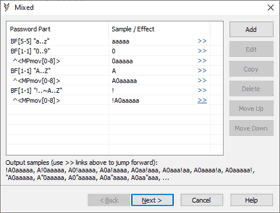
MPmov modification is designed to try one of the mixed attack parts in different / multiple positions.
Please check typing errors for other multi-position mods: MPdel, MPdbl, MPswp, MPdtl, MPdtf, MPswC, MPsub.
MPmov is applicable to any brute-force, dictionary or fixed part.
Target part (part before / preceding the mod) is moved within chars of all previous parts:
aa + bb + ZZ + MPmov = ZZaabb, aZZabb, aaZZbb, aabZZb, aabbZZ.
MPmov application range can be limited if necessary. It is set from position 0 (before first char) to MAX (after last char) by default.
aa + bb + ZZ + MPmov[0-2] = ZZaabb, aZZabb, aaZZbb
aa + bb + ZZ + MPmov[1-3] = aZZabb, aaZZbb, aabZZb
Several mods can be used to mix-in several different parts:
ab + * + MPmov + 0 + MPmov = 0*ab, *0ab, *a0b, *ab0, 0a*b, a0*b, a*0b, a*b0, 0ab*, a0b*, ab0*, ab*0
"Start from prior multi-position mod" option can be used to rebase MPmov range from preceding multi-position mod. The common application is to mix-in several equal parts (e.g. add several digits or several special chars) and avoid duplicates:
ab + 0 + MPmov + 0 + MPmov = 00ab, 00ab, 0a0b, 0ab0, 0a0b, a00b, a00b, a0b0, 0ab0, a0b0, ab00, ab00.
ab + 0 + MPmov + 0 + MPmov[+] = 00ab, 0a0b, 0ab0, a00b, a0b0, ab00.
Empty part to move or prior part(s) shorter than a starting move position can be filtered or passed with "Pass short or empty input as is" option.
Example 1 (very common password complexity policy):
Let's say there is no information about the password except for "0..9A..Za..z" charset and the fact that only one character is a digit and one is an uppercase letter. Letís say the password length is 8 chars.
Brute-force attack for 8 chars with "0..9A..Za..z" charset includes 62^8 (68 to the power of 8) passwords.
5 parts mixed attack:
<unknown> - brute-force, 6 chars, "a..z" charset.
<digit> - brute-force, 1char, "0..9" charset.
MPmov (applied to digit)
<uppercase letter> - brute-force, 1 char,"A..Z" charset.
MPmov (applied to uppercase letter)
This mixed attack includes 26^6 * (10*7) * (26*8) passwords. Actually it is around 2% from the full brute-force search.
Example 2:
Let's say one uppercase, one digit and one special char:
Brute-force attack for 8 chars with charset "0..9A..Za..z" + "!...~" includes 94^8 (>quadrillion) passwords!
7 parts mixed attack:
<unknown> - brute-force, 5 chars, "a..z" charset.
<digit> - brute-force 1 char, "0..9" charset.
MPmov (applied to digit)
<uppercase letter> - brute-force, 1 char, "A..Z" charset.
MPmov (applied to uppercase letter)
<special char> - brute-force, 1 char, "!..~" charset.
MPmov (applied to special char)
This mixed attack includes 26^5 * (10*6) * (26*7) * (32*8) passwords and it is less than 1% from the full brute-force search.