QuickBooks Internals | Security | Login
In contrast to many popular systems QuickBooks internal operations and procedures are almost completely unknown. We decided to publish some notes on basic QB workflow so you can connect this information with data provided by QuickBooks Forensics.
Under the hood, (starting from version 2007) QuickBooks company files are SQL Anywhere database files and QB is a GUI on top of database engine. This part is about the most basic login steps with single user configuration.
All users allowed to login are stored in table "ISYSUSER" (or "SYSUSERPERM" for old versions). Normal QB usernames are encoded as Hex strings, thus Admin (0x41 0x64 0x6D 0x69 0x6E) is stored as "41646D696E". This way one cannot use build-in credentials (e.g. "metadata_user", "backup_user") from QB interface.

![]()
Side note: There are number of SQL procedures stored in "ISYSPROCEDURE" / "SYSPROCEDURE" and used to control/modify some aspects of login, backup, etc. (e.g. "LoginProc") and table "CF_SYSINFO" holds configuration parameters. Parameters like "DropConnectionFromUser" come to light. "abmc_current_users" table is updated from "LoginProc".
Anyway it is outside the scope of this part, but they are easy to list and view with QuickBooks Forensics.
Back to "ISYSUSER". Password verification values are stored in "password" fields. From version 10 password verification is SHA-256 based (proprietary hashing algorithm in prior versions).
Thus username is converted to a Hex string, password is "prepared", hashed and compared to verification value and if they are equal user is logged in. QB uses internal access control methods, but for SQL Anywhere all users are equal in access rights. It is also easy to see how verification records can be replaced. Next level is Sensitive data records - Part 2 of our notes.
There is also one interesting table named "ABMC_TSAFE" with 1 row:
ADMIN_NAME - current Admin username as a Hex string.
challenge_text - The challenge question selected during Admin password change/setup.
ADMIN_KEY - RSA encrypted Admin password and challenge answer.
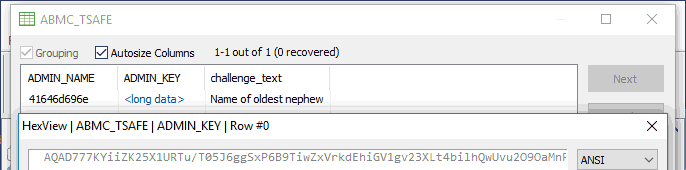
QuickBooks password reset feature is based on this backdoor. Data is sent to Intuit server to be decrypted, some sort of verification is performed based on license key and with a valid data decrypted Admin password can be changed instantly and full access restored.
There are several important security notes:
1) Decryption key recovery will make all other internal levels of security pointless.
2) Version 2007-2008 keys were recovered long ago.
3) And unfortunately backdoor key is constant for all versions 2009-2017 (US, CA, ...). If it is recovered or leaked than all company files and backups will be compromised.
All trademarks are the property of their respective holders.
