QuickBooks Internals | Security | Sensitive Data Keys
We took a look at QuickBooks login procedure in Part 1 and now we can check extra layer of security used in QuickBooks for number of records (CC Numbers, SSNs, Tax IDs, SINs, EIN, Bank accounts, etc.). Lets call them "sensitive data" records and encryption keys used "sensitive data" keys.
In multi-user environment key management system is required in order to control access to encrypted data, add / remove permissions, refresh keys, etc. QuickBooks generates Master key for every user with access to sensitive data. This key is used to decrypt user copy of sensitive data key. Master key itself is stored twice: ones encrypted based on user password and ones encrypted based on Admin password. Master keys are permanent.
After login user master key records are read from "abmc_master_key" table. 8 bytes "seed_value" is combined with user password to decrypt master key.
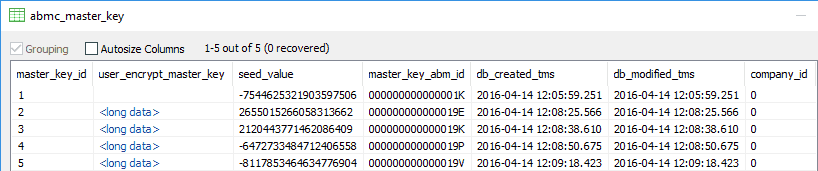
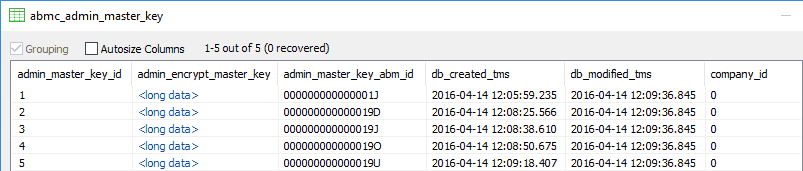
Admin password encrypted copy of user master key is stored in "abmc_admin_master_key" table. There is no reason to save 2 copies of Admin key so Admin master key is kept in "abmc_admin_master_key" only.
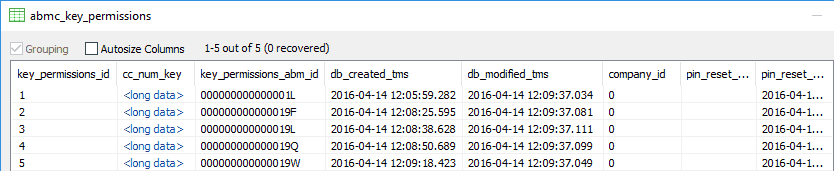
Actual keys necessary to decrypt protected records are stored in table "abmc_key_permissions" : "cc_num_key".
This is standard and effective system. It allows User to:
1) Access its master key and its copy of sensitive data key.
2) If user password is changed than only one record in "abmc_master_key" have to be fixed.
At the same time Admin can:
1) Access all master keys, so users copies of sensitive data key can be replaced, changed, deleted.
2) Replace user password along with copies of encrypted master key.
Unfortunately there are number of bugs in this system and some redundant extra tables compromising security you can see with QuickBooks Forensics in Part 3 of our notes.
All trademarks are the property of their respective holders.
